Introduction
Cybersecurity researchers have identified a critical security vulnerability in Replicate, an AI-as-a-service provider, which could have enabled threat actors to access proprietary AI models and sensitive information. This article explores the nature of the vulnerability, the method of exploitation, and the implications for AI-as-a-service platforms.
Discovery and Nature of the Vulnerability
According to a report by cloud security firm Wiz, the vulnerability could have allowed unauthorized access to AI prompts and results for all of Replicate's platform customers. The flaw is rooted in the way AI models are typically packaged. These models are often in formats that permit arbitrary code execution, a loophole that can be exploited for cross-tenant attacks using a malicious model.
Replicate utilizes an open-source tool called Cog to containerize and package machine learning models, which can then be deployed in a self-hosted environment or directly on Replicate. Wiz's researchers discovered that by creating a rogue Cog container and uploading it to Replicate, they could achieve remote code execution on the service's infrastructure with elevated privileges.
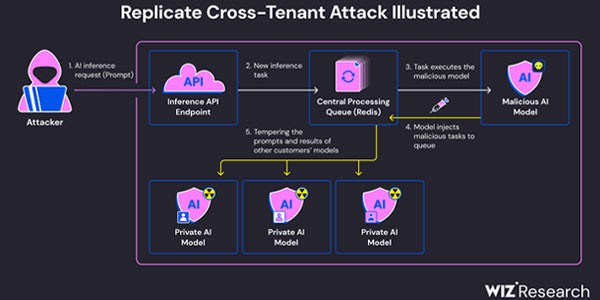
Exploitation Methodology
The attack leveraged an existing TCP connection associated with a Redis server instance within a Kubernetes cluster hosted on the Google Cloud Platform. This allowed the researchers to inject arbitrary commands into the system. The centralized Redis server, used as a queue to manage multiple customer requests and their responses, was found to be a weak point that could be abused to facilitate cross-tenant attacks. By tampering with this process, rogue tasks could be inserted, impacting the results of other customers' models.
Implications and Risks
These rogue manipulations pose significant risks to the integrity, accuracy, and reliability of AI-driven outputs. An attacker could potentially query private AI models, exposing proprietary knowledge or sensitive data involved in the model training process. Additionally, intercepting prompts could reveal sensitive data, including personally identifiable information (PII).
The researchers pointed out that this code-execution technique is likely a pattern, with companies and organizations running AI models from untrusted sources, despite the potential for these models to be malicious.
Mitigation and Response
The vulnerability was responsibly disclosed to Replicate in January 2024 and has since been addressed. There is no evidence that the vulnerability was exploited in the wild to compromise customer data. This disclosure follows a similar incident reported by Wiz involving platforms like Hugging Face, where risks allowed for privilege escalation, cross-tenant access, and CI/CD pipeline takeovers.
Conclusion
The discovery of this critical security flaw in Replicate highlights the significant risks posed by malicious models to AI-as-a-service providers. The potential impact of such vulnerabilities is devastating, as attackers could gain access to millions of private AI models and applications stored within these platforms. It underscores the importance of robust security measures and thorough vetting of AI models to protect sensitive data and maintain the integrity of AI-driven outputs.










0 Comments