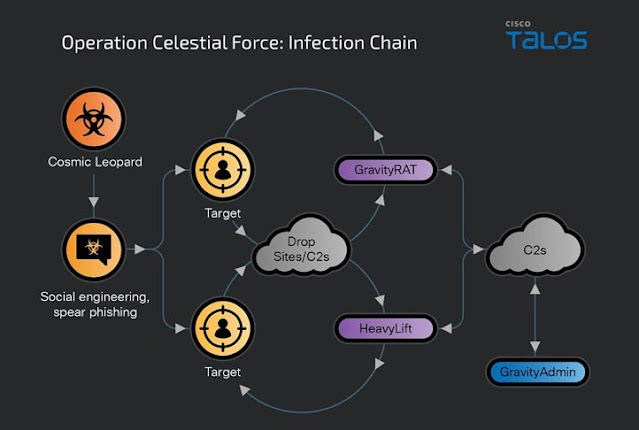
Since at least 2018, a sophisticated malware campaign known as Operation Celestial Force has been actively targeting entities in the Indian subcontinent. This operation involves the use of multiple malware tools, including GravityRAT for Android, and a Windows-based malware loader dubbed HeavyLift. Administered through a standalone tool called GravityAdmin, this campaign has been attributed to a threat actor known as Cosmic Leopard, which shares some tactical similarities with another known adversary, Transparent Tribe. The persistent and evolving nature of this campaign underscores its significant success and adaptability in compromising sensitive targets.
Introduction to Operation Celestial Force
Operation Celestial Force, identified and analyzed by cybersecurity researchers from Cisco Talos, has been linked to Pakistani threat actors. This long-running operation utilizes a suite of malware tools designed to target various operating systems, demonstrating a high level of sophistication and adaptability. The primary tools employed in this campaign are GravityRAT, an Android malware, and HeavyLift, a malware loader for Windows systems. These tools are managed using GravityAdmin, a comprehensive administration tool that coordinates the malware's activities.
GravityRAT: The Multifaceted Malware
GravityRAT first emerged in 2018 as a Windows malware targeting Indian entities through spear-phishing emails. Its primary function was to harvest sensitive information from compromised systems. Over time, GravityRAT has evolved into a multi-platform tool, now capable of infecting Android and macOS devices. This evolution highlights the threat actor's continuous efforts to expand the malware's reach and effectiveness.
In recent years, researchers from Meta and ESET uncovered the ongoing use of GravityRAT's Android version, which targets military personnel in India and the Pakistan Air Force. The malware disguises itself as legitimate cloud storage, entertainment, and chat applications, making it challenging for targets to detect its malicious intent.
HeavyLift: The Windows-Based Malware Loader
HeavyLift, the newly identified component of Operation Celestial Force, is an Electron-based malware loader designed to target Windows systems. Distributed via malicious installers, HeavyLift shares similarities with previous versions of GravityRAT documented by Kaspersky in 2020. Once executed, HeavyLift collects and transmits system metadata to a command-and-control (C2) server, periodically polling the server for new payloads to execute.
GravityAdmin: The Command Center
GravityAdmin serves as the command center for Operation Celestial Force, providing a user-friendly interface for managing the campaign. The tool consists of multiple inbuilt user interfaces (UIs) corresponding to specific codenamed campaigns. For instance, "FOXTROT," "CLOUDINFINITY," and "CHATICO" are associated with Android-based GravityRAT infections, while "CRAFTWITHME," "SEXYBER," and "CVSCOUT" pertain to attacks deploying HeavyLift.
GravityAdmin facilitates the coordination of various malware components, establishing connections with GravityRAT and HeavyLift's C2 servers. This centralized control allows the threat actors to efficiently manage their operations and respond to new opportunities and challenges.
Tactical Overlaps with Transparent Tribe
The cybersecurity community has noted that Cosmic Leopard, the adversary behind Operation Celestial Force, exhibits tactical overlaps with Transparent Tribe, another known threat actor. Both groups employ similar techniques, such as spear-phishing and social engineering, to establish trust with their targets. Once trust is established, the attackers direct their targets to malicious websites that prompt them to download seemingly benign programs, which then deploy GravityRAT or HeavyLift, depending on the target's operating system.
Conclusion
Operation Celestial Force represents a persistent and evolving threat to entities in the Indian subcontinent. The campaign's success can be attributed to the sophisticated malware tools employed, including GravityRAT and HeavyLift, and the centralized management provided by GravityAdmin. The ongoing nature of this operation, coupled with its ability to adapt and expand its malware suite, underscores the importance of continued vigilance and advanced cybersecurity measures. As threat actors continue to refine their tactics, it is crucial for organizations and individuals to stay informed and proactive in protecting their digital assets.
By understanding the complexities and strategies behind Operation Celestial Force, cybersecurity professionals can better anticipate and mitigate future threats, ensuring the safety and security of sensitive information and critical systems.










0 Comments