Introduction
In recent revelations by cybersecurity researchers at Sophos, a shadowy campaign codenamed Crimson Palace has cast a spotlight on covert Chinese state-sponsored cyber espionage activities targeting a prominent government entity in Southeast Asia. This operation, characterized by its complexity and prolonged duration, underscores the persistent threat posed by sophisticated cyber adversaries.
The Scope of Crimson Palace
Crimson Palace operates through three distinct clusters—Alpha, Bravo, and Charlie—each exhibiting unique tactics and tools aimed at achieving persistent access and covert data exfiltration. These clusters, spanning from March 2023 to April 2024, demonstrate a coordinated effort under a unified command structure, highlighting the strategic alignment of multiple cyber actors towards common objectives.
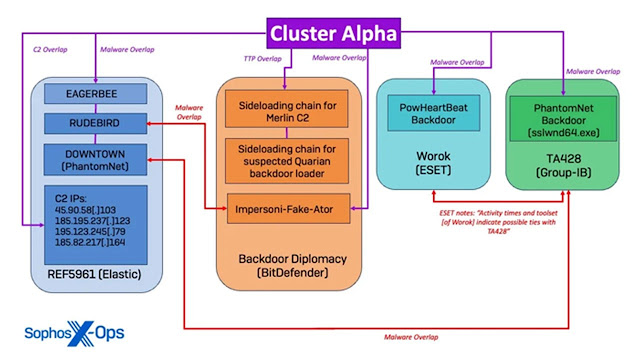
Cluster Alpha: Engaging in activities reminiscent of prior state-sponsored intrusions, Cluster Alpha focused on mapping server subnets, enumerating administrator accounts, and probing Active Directory infrastructure. This phase laid the groundwork for subsequent operations, leveraging undisclosed malware like PocoProxy to ensure long-term access.
Cluster Bravo: Operating with similarities to known cyber groups like Unfading Sea Haze, Cluster Bravo prioritized lateral movement using legitimate credentials, while deploying sophisticated tools such as EtherealGh0st for command and control. This phase highlights the adaptability of the attackers in navigating targeted networks undetected.
Cluster Charlie: The most protracted phase, spanning multiple months, Cluster Charlie introduced novel techniques like DLL side-loading and the use of HUI Loader to distribute Cobalt Strike. This phase not only sustained ongoing operations but also expanded the arsenal of tools employed, reflecting an evolving and dynamic threat landscape.
Technical Sophistication and Evasion Techniques
The perpetrators behind Crimson Palace employed a spectrum of advanced evasion tactics to evade detection and maintain persistence within compromised systems. Techniques such as DLL manipulation in memory, abuse of antivirus software for sideloading, and the strategic deployment of obscure malware families like NUPAKAGE and PowHeartBeat underscored the campaign's technical prowess and operational agility.
Implications and Global Response
The emergence of Crimson Palace coincides with a broader escalation in state-sponsored cyber activities attributed to China, as noted by cybersecurity advisories from various nations. The operation's targeting of critical infrastructure and sensitive governmental sectors underscores the strategic geopolitical implications of cyber warfare and espionage in the modern age.
Conclusion
The Crimson Palace operation, meticulously detailed by Sophos researchers, serves as a stark reminder of the persistent cyber threats facing governments and organizations worldwide. As cybersecurity defenses evolve, so too must international cooperation and defensive measures to mitigate the impact of such sophisticated attacks. The need for enhanced vigilance, technological resilience, and diplomatic engagement remains paramount in safeguarding against future incursions into sensitive networks and data repositories.
In essence, Crimson Palace stands as a testament to the evolving capabilities of state-sponsored cyber adversaries and the imperative for concerted global efforts to bolster cybersecurity frameworks in an increasingly interconnected world.










0 Comments