Introduction
Cybersecurity threats continue to evolve as attackers adapt and employ sophisticated tools for malicious purposes. Recent findings by Cisco Talos reveal a troubling trend: threat actors are using a tool initially intended for red teaming exercises to deliver malware. This tool, known as MacroPack, is designed to generate various formats, including Office documents and Visual Basic scripts, for penetration testing and social engineering assessments. However, malicious entities are repurposing it to launch attacks, signaling the constant evolution of their tactics.
What is MacroPack?
MacroPack, developed by French programmer Emeric Nasi, is a payload generation framework used for ethical hacking. It was originally created to assist in penetration testing by generating payloads in multiple formats such as Office documents, Visual Basic scripts, and Windows shortcuts. These payloads are often used in social engineering campaigns or red team exercises, helping security professionals simulate attacks and assess vulnerabilities within systems.
Despite its intended ethical use, Cisco Talos has observed that threat actors are now leveraging MacroPack to deliver malware. This includes sophisticated payloads such as Havoc, Brute Ratel, and a new variant of PhantomCore, a remote access trojan (RAT) associated with the hacktivist group Head Mare.
Unveiling Malicious Use of MacroPack
Cisco Talos uncovered several artifacts related to MacroPack uploaded to VirusTotal, a popular file analysis platform, from regions such as China, Pakistan, Russia, and the United States. These artifacts revealed a common pattern: attackers using MacroPack to deliver a variety of malware payloads. One significant finding involved non-malicious Visual Basic for Applications (VBA) subroutines present in all the malicious documents.
According to Talos researcher Vanja Svajcer, these subroutines were never obfuscated, nor had they been seen in any other malware samples before. Their consistent presence across multiple malicious documents suggests that threat actors may be relying on MacroPack's built-in features to evade detection.
Diverse Lure Themes and Techniques
One notable aspect of these attacks is the varied nature of the lure themes used to trick victims. Some documents appear as simple instructions to enable macros, while others mimic official-looking documents from military or governmental organizations. This indicates that different groups of threat actors are likely involved in these attacks, each customizing their social engineering techniques to suit their targets.
Moreover, some documents exploit advanced features of MacroPack to avoid anti-malware detection. By using techniques like Markov chains to create convincing functions and variable names, attackers can conceal the malicious nature of their payloads. This allows them to bypass heuristic detection methods, making their attacks even harder to identify.
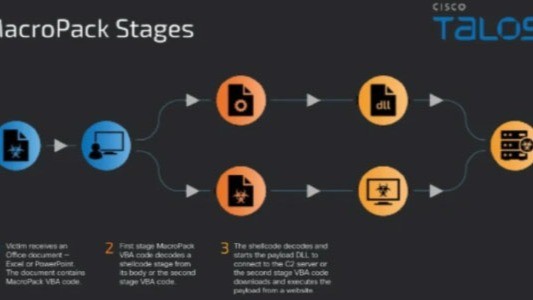
The Attack Process
The attack chains observed between May and July 2024 follow a structured three-step process. First, attackers send a booby-trapped Office document embedded with MacroPack-generated VBA code. Once the user opens the document and enables macros, the VBA code decodes a secondary payload. This payload, in turn, fetches and executes the final malware on the victim's system. This multi-stage approach allows attackers to avoid detection at each stage while gradually deploying the malware.
Conclusion
The findings by Cisco Talos highlight how threat actors are increasingly adapting legitimate tools like MacroPack for nefarious purposes. By leveraging its payload generation capabilities, they can create highly targeted and sophisticated attacks that evade traditional detection methods. As attackers continue to refine their tactics, cybersecurity professionals must stay vigilant, ensuring that defenses evolve in response to these emerging threats. The use of tools designed for ethical hacking in malicious campaigns emphasizes the importance of continuously updating and strengthening cybersecurity measures.










0 Comments